CMAC creates a message authentication code from an encryption primitive. The most common is the AES-CMAC, which is described fully in RFC 4493. It involves operating the AES operation in cipher-block chaining mode, where each 16-byte chunk of the original plaintext is fed to the AES encryption operation in turn and combined with the output of the previous block’s encryption. There is one additional wrinkle – the final block (or partial block) of plaintext is XORed with a “subkey” before passing through the encryption stage. There are two subkeys derived from the AES key (through another AES encryption and some bitwise operations). One of these two subkeys is selected for use in the final AES operation depending on whether the final block is complete or needed to be padded.
However, an attacker does not need to care about all the details of AES, as the very first operation performed is to XOR the plaintext with the key and feed it through a non-linear lookup table.
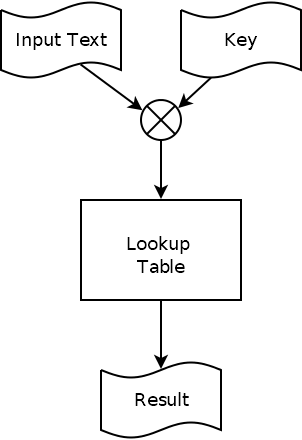
Using power analysis it is possible, by observing the power consumed by the output of this operation, to extract the key. Doing this requires the attacker to control the first block that is passed in so that they can correlate changes of power with changes of plaintext.
