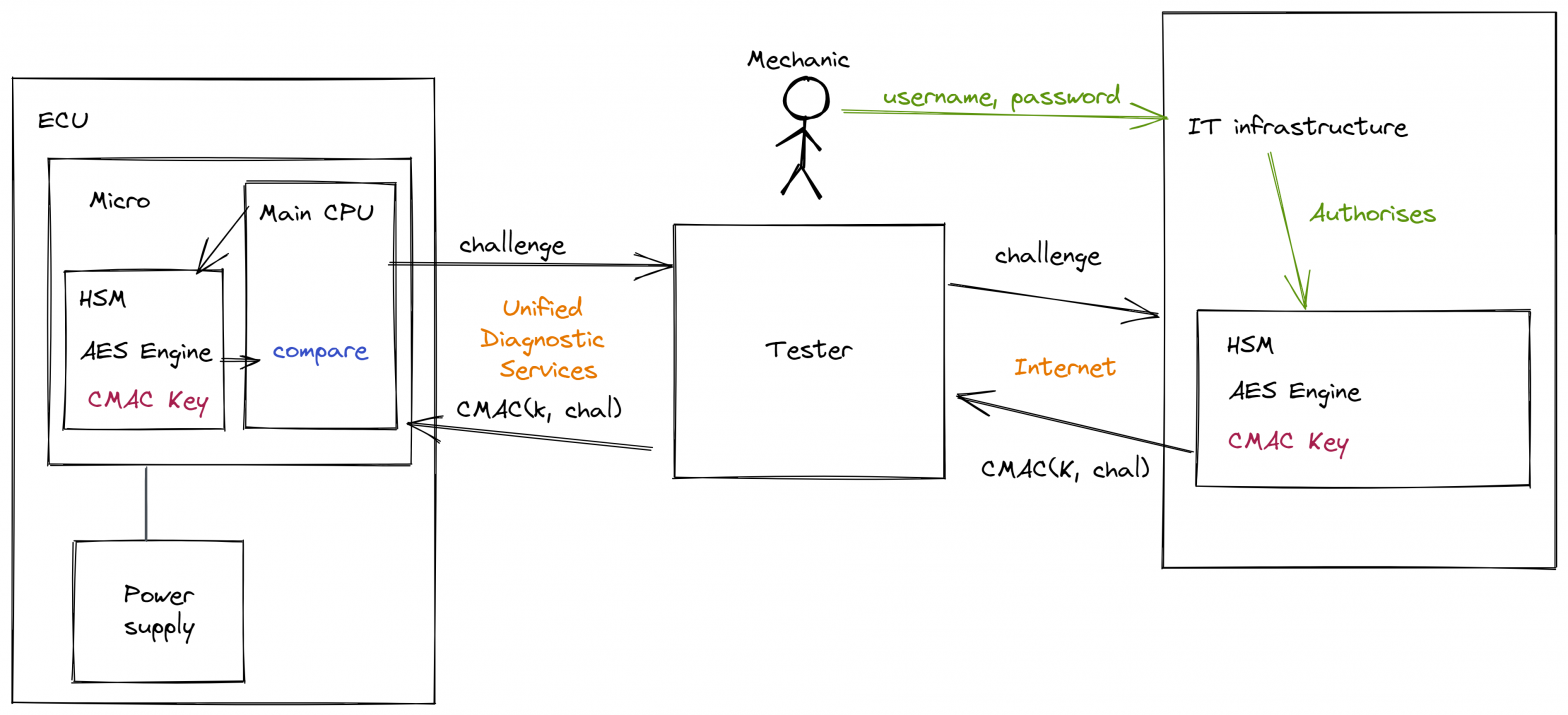
In normal operation, the mechanic uses a piece of equipment which is colloquially known simply ‘a tester’ which talks to the ECU using the ISO-14229 UDS services. Often this is over a CAN-bus but can also be over Flexray, LIN, Ethernet etc. When the mechanic needs to access some secured aspect of the ECU they engage in a challenge and response protocol with the ECU. In this case, the tester contacts some infrastructure (run by the vehicle manufacturer or the ECU supplier) to get the response. The mechanic will have previously authenticated themselves to this infrastructure in order to gain authorisation.
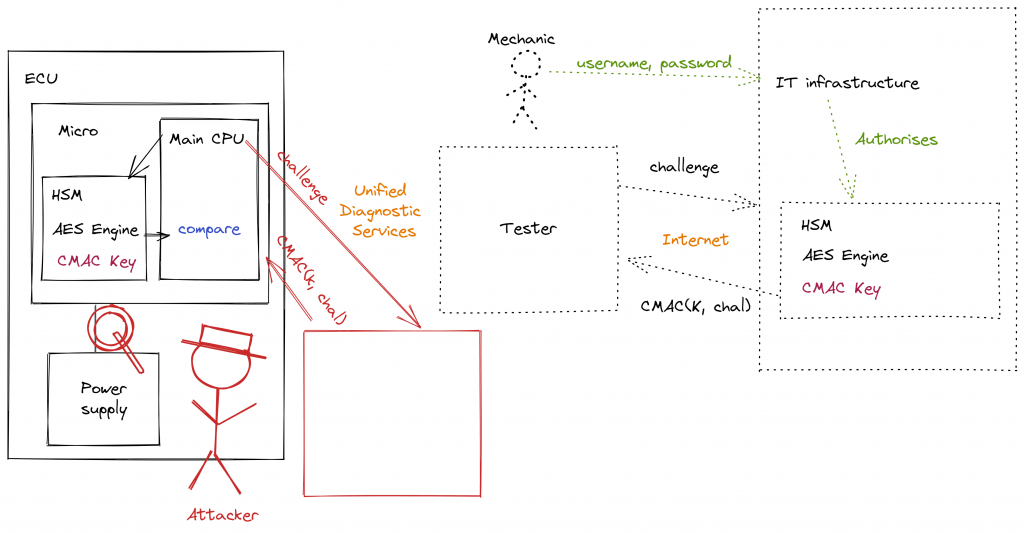
In order to attack such a system the attacker replaces the tester with their own device which requests challenges and sends random responses. By monitoring the power consumption of the microcontroller (either directly measuring the current consumption, or indirectly with a field-probe) the attacker can determine when the CMAC operation is taking place. Furthermore, by correlating this power consumption profile with the data over which the CMAC is operating, they can extract the keys used in the AES operations. Once these keys become known, they can create the correct responses independently and then unlock features or services on the ECU.